implementing a filter to remove flooded packets before they reach the host is a countermeasure to which form of attack?
Answers
Implementing a filter to remove flooded packets before they reach the host is a countermeasure to a Distributed Denial of Service (DDoS) attack.
A DDoS attack occurs when a large number of compromised devices flood a target system with a high volume of traffic, overwhelming its resources and making it inaccessible to legitimate users. One common type of DDoS attack is a flood attack, where the attacker sends an excessive amount of traffic to the target system, often using multiple sources. By implementing a filter to remove flooded packets, the system can identify and discard the malicious traffic associated with a DDoS attack. This filtering process can be based on various criteria, such as the source IP address, packet rate, or traffic patterns, allowing the system to drop or redirect the excessive traffic before it reaches the intended host. This countermeasure helps mitigate the impact of the attack by reducing the burden on the target system's resources and ensuring that legitimate traffic can reach its destination.
Learn more about countmeasure here : brainly.com/question/28053850
#SPJ11
Related Questions
________ modems use a portion of a voice telephone line to maintain a connection to offer immediately-available broadband access.
Answers
Dial-up modems maintain a connection to provide instantly accessible broadband access by using a portion of a voice telephone line.
Explain about the Dial up modems?Using a modem, dial-up is a method of connecting to the internet on a computer using the public telephone network. Although high-speed internet has long been a popular option, dial-up service is still readily available in many locations. Technically, a dial-up connection functions much the same way as a regular phone call. except that instead of two individuals, it joins computers at either end.
Next came cable modems, which could transmit data at far faster rates than dial-up and (at the time) ADSL modems by using already-existing television (coaxial) lines. Early cable modems were basic and only allowed one device to be connected at a time because there were no additional services to allow sharing of the internet connection.
To learn more about Dial up modems refer to:
https://brainly.com/question/29448526
#SPJ1
which circut is a series circut?
Answers
In a series circuit, the components are connected end-to-end
What is a Series Circuit?A series circuit is a circuit in which the components (such as resistors, capacitors, and inductors) are connected in a single path, so that the same current flows through all the components.
In other words, the components are connected end-to-end, and there are no branches or parallel connections in the circuit.
P.S: Your question is incomplete, so a general overview was given.
Read more about series circuit here:
https://brainly.com/question/19865219
#SPJ1
Challenge 13 - Create a program to ak the uer their age and if it i between 4 and 16 it hould output
"You are in chool", otherwie output "You are not of chool age"
Answers
Answer:
age = int(input("Enter your age: "))
if age >= 4 and age <= 16:
print("You are in school")
else:
print("You are not in school age")
Explanation:
since you didnt mention the program you’re using, im going to answer it using python. if there's anything to amend let me know!
_____ is the feature that allows you to quickly advance cell data while filling a range of cells.
A. Auto Fill
B. AutoCopy
C. FillAuto
D. CopyAuto
Please no files just type the answer, thanks!
Answers
Answer:
A. Auto Fill
Explanation:
Auto Fill is the feature that allows you to quickly advance cell data while filling a range of cells.
Can you write a story about any princess?
Mark brainiest. Please
Answers
Okay well here's a short one. The main problem in Cinderella is that she wants to go to the ball but her stepsisters prevent her from going because they wanna marry the prince-
Cinderella is a beautiful kind daughter sees the world upside down when her mother dies and so her father in pain marries another woman who is wicked and the name is "Lady Termaine" she has two cruel daughters who get so jealous so easily. The daughters are named Drizella & Anastasia.
achievements of science in our society
Answers
Answer:
Science has paved the way for so many discoveries throughout the decades. Some big science achievements in society that could be remarked are;
Lunokhod 1:
Lunokhod 1 was a spacecraft that landed first remote controlled robot that landed on the moon by the soviet union. the robot weighted just under 2,000 pounds and was designed to operate for 3 months. Lunokhod was operates by a 5 person team on Earth.
The First Ultrasound:
The first ultrasound was introduced by Ian Donald. He used a one dimensional A-mode to measure the parietal dimeter of a fetal head and two years later Donald's and Brown, a co-worker, presented the ultrasound of a female tumor. Donald's and Browns work paved the way for ultrasounds in medical science.
Rapid Covid Vaccinee Development:
One of the biggest achievements if the rapid development of the vaccinee for Covid-19, with the deadly virus spreading back in 2020, it took less than 2 years to develop a vaccine when normally, it takes 10-15 years. Medical science has come a long way, and this is a huge example of it.
When an operator has two operands of different data types, c++ always converts them both to double before performing the operation.
a. true
b. false
Answers
When an operator has two operands of different data types, c++ always converts them both to double before performing the operation is false statement.
What is operands and example?In regards to computer programming, an operand is seen as a term that is often used to tell more any object that is often capable of being altered.
A good example, in "1 + 2" the "1" and "2" are said to be operands and the plus symbol is known to be called the operator.
In regards to mathematics, an operand is seen as the object of a any form any mathematical operation.
Therefore, When an operator has two operands of different data types, c++ always converts them both to double before performing the operation is false statement.
Learn more about operands from
https://brainly.com/question/27014457
#SPJ1
Draw a circuit with a 12-volt battery and two resistors(100 ohms and 200 ohms) in parallel. What is the total resistance of the circuit?
Answers
The total resistance in the circuit is 66.67 ohm.
What is a circuit?The circuit is a path designed for the flow of current. We can see that the resistors are connected to a common junction (in parallel) as shown in the image attached to this answer.
The total resistance is obtained from;
1/Rt= 1/R1 + 1/R2
1/Rt= 1/200 + 1/100
1/Rt= 0.005 + 0.01
Rt = 66.67 ohm
Learn more about resistance:https://brainly.com/question/21082756
#SPJ1

Answer:
The total resistance in the circuit is 66.67ohm
what is the single most important part of data recovery
Answers
The single most important part of data recovery is ensuring that the data is not overwritten or further damaged during the recovery process.
The single most important part of data recovery is preserving the integrity of the original data and ensuring that it is not overwritten or further damaged during the recovery process. This is crucial because any additional changes or modifications to the data can potentially make the recovery process more challenging or even render the data irretrievable.
When data is lost or inaccessible, it is essential to immediately stop any actions that may write or modify data on the affected storage media. This includes refraining from saving new files, installing software, or performing any activities that could alter the data on the storage device. By avoiding such actions, the chances of successful data recovery are significantly increased.
Overwriting or further damaging the data can occur when recovery attempts are made without proper knowledge, tools, or expertise. It is recommended to consult professional data recovery services or utilize specialized data recovery software that follows best practices to avoid inadvertently causing harm to the data.
By prioritizing data preservation and minimizing any potential changes to the original data, the data recovery process can be conducted more effectively, increasing the likelihood of successfully retrieving the lost or inaccessible information.
To learn more about data recovery visit : https://brainly.com/question/31526761
#SPJ11
what is the primary difference between switchkvm and switchuvm functions?
Answers
The primary difference between switchkvm and switchuvm functions is that switchkvm is responsible for switching the kernel's virtual memory mapping, while switchuvm is responsible for switching the user's virtual memory mapping.
The switchkvm function is used in the Verilog programming language. This function is used to switch the input/output of a module. It is used to switch the input/output between different pins or buses. The switchkvm function is used when it is necessary to change the connection between the inputs and outputs of a module.The switchuvm function is used in the Universal Verification Methodology (UVM).
Learn more about switchkvm: https://brainly.com/question/13439312
#SPJ11
Your school is hosting a diving contest, and they need a programmer to work on the scoreboard! Your job is to calculate each diver's total after the three judges hold up their individual scores. Write the function calculate_score which takes a tuple of three numbers from 0 to 10 and calculates the sum. A perfect dive is worth 30 points, a belly flop is worth 0. For example: calculate_score((10, 10, 10)) # => 30 calculate_score((9, 9, 6)) # => 24
Answers
Answer:
def calculate_score(setss):
num1, num2, num3= setss
if num1 >= 0 and num1 <=10 and num2>= 0 and num2<=10 and num3>= 0 and num3<=10:
print(num1+ num2+num3)
else:
print("Out of range")
Explanation:
I've added the full source code as an attachment, where I used comments as explanation
in the dbms_ddl package, the ____ procedure creates statistics for database objects to be utilized to enhance performance. a. alter_compile b. alter_ddl c. analyze_ddl d. analyze_object
Answers
The procedure that creates statistics for database objects to enhance performance in the dbms_ddl package is the analyze_object procedure.
This procedure gathers and stores statistics about the data distribution and storage characteristics of tables, indexes, and clusters. These statistics are then utilized by the query optimizer to determine the most efficient execution plan for SQL statements. The analyze_object procedure can be run on individual objects or multiple objects at once. By regularly running this procedure, database administrators can ensure that the optimizer is always working with up-to-date statistics, which can lead to significant improvements in query performance.
learn more about database objects here:
https://brainly.com/question/10052879
#SPJ11
Write down the difference between Sub... end sub and function... end function statement.
any 3 points, please
Answers
A sub does something but doesn't give something back. A function provides a value representing the tasks completed. Subs come in many different types and can be recalled from anywhere in the program.
What is sub and end sub in VBA?A Sub procedure is a collection of Visual Basic statements that are delimited by the Sub and End Sub statements and that carry out tasks without producing a result. A calling procedure may give constants, variables, or expressions as inputs to a sub process.
Various processes are used in Visual Basic, including: Sub Procedures carry out tasks but do not provide the calling code with a value in return. Sub procedures known as "event-handling procedures" run in response to an event triggered by a user action or by a program occurrence.
Thus, A sub does something but doesn't give something back.
For more information about sub and end sub in VBA, click here:
https://brainly.com/question/26960891
#SPJ1
what device is most likely installed in your computer to connect it to a wired or wireless network?
Answers
A router is a piece of hardware that enables you to create a home network, or many computers and other devices connected to a single Internet connection.
What allows your PC to join a wired network?To the port on the back of the desktop computer, attach a LAN cable. Use a LAN adapter to connect if your laptop lacks a side-mounted LAN port.
What exactly is a computer's Internet connection device?Normally, a modem connects to a router, which takes internet access from the modem and distributes it to other networked devices. For connectivity, modems can make use of Ethernet cable, DSL, fiber, or wireless technologies.
To know more about network visit:-
https://brainly.com/question/14276789
#SPJ4
TRUE OR FALES
1.Windows 98 is not a GUI-based operating system.
Answers
Answer:
TRUE
Explanation:
t is a graphical user interface (GUI) based operating system. Which makes our operation interactive and easy to use. Windows 98 is an improved version of Windows 95. Main feature in windows 98 is its 'Desktop'.
Yelena has created timings within her slide show, and she wants to verify that each slide has the correct timing. In which view in PowerPoint can she do this? a. Normal view b. Outline view c. Slide Master view d. Slide Sorter view
Answers
Yelena has created timings within her slide show, and she wants to verify that each slide has the correct timing in the Slide Sorter view in PowerPoint.
The correct answer to the given question is option d.
Viewing the Slide Show in Power Point.The default view of the presentation is in Normal view. In this view, we can add content and make modifications to the slides. However, we can also view the slides in various other ways. Let's have a look at each view:
Normal view: This view is the default view and is the view in which we can add and modify the slide content. We can also add and modify slide animations and transitions here.
Outline view: In this view, we can view the text content of the presentation in outline form, which makes it easy to organize the presentation.
Slide Sorter view: This view allows us to view all the slides in the presentation simultaneously, which makes it easy to rearrange the slides or change their timings.Notes Page view: In this view, we can view the speaker notes associated with each slide.
Slide Master view: In this view, we can create and modify slide layouts and templates.The Slide Sorter view allows us to see all the slides in the presentation at once, so it is the best view to use to verify the timings for each slide. We can use the controls at the bottom of the Slide Sorter view to modify the timing of each slide.
For more such questions on PowerPoint, click on:
https://brainly.com/question/28220859
#SPJ8
Sunil’s basketball coach asks him to prepare a presentation for his teammates on the proper way to shoot a basketball. After researching the topic online, Sunil decides to add a visual aide to his report.
Which visual aide is the best fit for Sunil’s presentation?
a podcast describing how to shoot a basketball
a video tutorial showing how to shoot a basketball
a graph showing how many players shot a basketball
a sound bite describing a player shooting a basketball
Answers
Answer: a video tutorial showing how to shoot a basketball
Explanation:
It will show them how to shoot the basketball
Answer:
a video
Explanation:
What elements collect input?
What items display output?
Do you think there are elements that can do both?
Answers
Answer:
input devices : keyboard, touch , mouse
output devices : microphone monitor, printer
Cameras and Modem can be both output and input.
Please help!!!!!!! 50 POINTS!!!!
Select ALL correct answers (there might be more than one)
In attempts to improve their contribution to the environment, a company decides to adapt green computing. Which of these techniques will contribute to green computing?
A. Virtualization will help the company cut down on their hardware requirements.
B. Grid computing will also help reduce the number of machines required to run a process.
C. Recycling old systems is a more environmentally friendly way of disposing of old systems.
D. Autonomic computing can also benefit green computing since automated systems are more environmentally friendly.
Answers
Answer:
A,D,C,B are the correct answers
Explanation:
Hope this helps:)
Answer:
Behold.
Explanation:
The comment directly to the answer is likely completely right, if it isn't, then its at least half right.

You have just been hired as a Level 1 PC Support Technician by Acme Products. Part of your job responsibilities include performing limited tasks on company workstations. You need to create a local account for a user on a computer running Windows Vista. You also need to install a printer for that user. What type of account must you have on the Windows Vista computer in order to complete your assigned work with limited access?
Answers
You need a userguest account on a Windows Vista PC in order to finish your given tasks with restricted access.
What kind of account allows for total computer access?During the Windows installation, the Administrator account is the first to be established. The local device's services, directories, files, and other resources are completely under the authority of the Administrator account.
What are the three different kinds of Windows user accounts?For ordinary computing, standard user accounts are used. Only utilize administrator accounts when absolutely essential because they provide you the most authority over a machine. Those who only need temporary access to a computer are the main target audience for guest accounts.
To know more about Windows Vista visit :-
https://brainly.com/question/12973188
#SPJ4
Drive
0101
0102
0103
0104
0105
0106
0107
0108
0109
0110
0111
0112
0113
0114
0115
0166
Sorting Minute
True
102
162
165
91
103
127
112
137
102
147
163
109
91
107
93
100
An Excel table can help
you organize your data in
preparation for using it
with charts and other
analysis tools.
Copyright © 2003-2022 International Academy of Science. All Rights Reserved.
False
Answers
Answer:
What
Explanation:
True
what is the main task of the project manager
Answers
Answer:
to handle day to day operations of a project
Explanation:
Answer: to handle the day to day operations of the project
Explanation:
With respect to iot security, what term is used to describe the digital and physical vulnerabilities of the iot hardware and software environment?
a. Traffic Congestion
b. Device Manipulation
c. Attack Surface
d. Environmental Monitoring
Answers
Answer: Answer Surface
Explanation:
Explain the "no read-up, no write-down approach." (Bell-LaPadula model)
Answers
The Bell-LaPadula policy is provided through a computer system. The virus spreads if the virus is deployed on the system at a low level.
What is a computer virus?When run, a computer virus is a sort of computer program that repeats itself by altering other computer programs and inserting its own code. If the replication is successful, the afflicted regions are considered to be "infected" with a computer virus, a term inherited from biological viruses.
The computer may act weirdly, glitch, or operate abnormally slowly if you have an infection.
Therefore, The Bell-LaPadula policy is provided through a computer system. The virus spreads if the virus is deployed on the system at a low level.
Learn more about computer on:
https://brainly.com/question/13805692
#SPJ1
A user submitted a support ticket that states all of the printouts from a laser printer appear to have double images imposed on them. A review of past printer support tickets shows that a maintenance kit has not been installed in more than a year. Which of the following printer consumables is MOST likely causing the issue?
A. Separation pad
B. Transfer roller
C. Ink cartridge
D. Fuser
Answers
The fact that a maintenance kit has not been installed in over a year is also a clue that the fuser may be the cause of the problem. Maintenance kits typically include replacement parts for the fuser, such as a fuser roller or heating element, which can wear out over time and cause printing issues.
Therefore, the correct answer is D. Fuser.
Option d is correct, Fuser is the printer consumables which is most likely causing the issue.
The issue described, where printouts have double images imposed on them, is a common symptom of a faulty fuser in a laser printer.
The fuser is responsible for bonding toner to the paper, and if it is not functioning properly, it can cause double images or smudging on the printouts.
Given the lack of maintenance kit installation for over a year, it is highly likely that the fuser needs to be replaced or repaired.
To learn more on Fuser click:
https://brainly.com/question/14902244
#SPJ2
What am I doing wrong please HELP
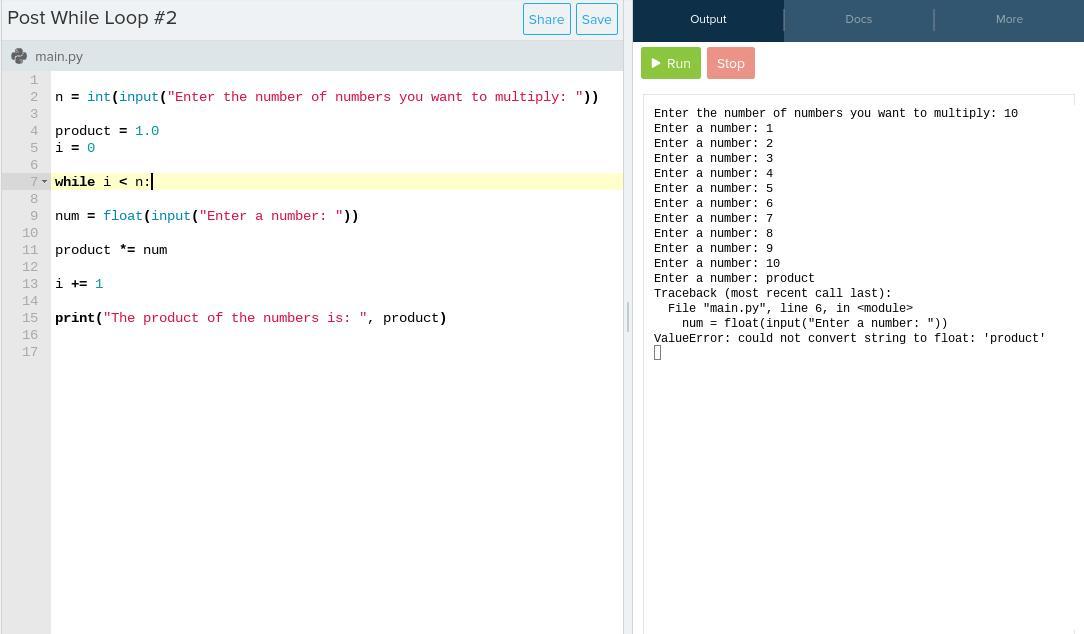
Answers
I think the problem here is that the statements in the body of the while loop are not indented. It works for me with the indentation, as shown in the screenshot attached.

Which of the following might increase economic efficiency in a fast-food restaurant?
long lines for customers
flexible hours for workers
not enough workers to take care of customers
all of the above
Answers
Answer:
I think B.
Explanation:
It may be wrong but, B makes the most since. I don't know how, sorry if I'm wrong!
Answer:
look
Explanation:
The labor market continues to recover, but a stubbornly high rate of underemployment persists as more than five million Americans are working part-time for economic reasons (U.S. BLS 2015a; 2015b). Not only are many of this type of underemployed worker, by definition, scheduled for fewer hours, days, or weeks than they prefer to be working, the daily timing of their work schedules can often be irregular or unpredictable. This both constrains consumer spending and complicates the daily work lives of such workers, particularly those navigating through nonwork responsibilities such as caregiving. This variability of work hours contributes to income instability and thus, adversely affects not only household consumption but general macroeconomic performance.
The plight of employees with unstable work schedules is demonstrated here with new findings, using General Social Survey (GSS) data. These findings (as well as key findings from other research) are highlighted below.
Who is your favorite Funtime Anamatronic?
Answers
Answer:
ur mom
Explanation:
jk it's prb something like foxy
Which command would you use to copy all files and subdirectories in a directory, including empty subdirectories?.
Answers
Use the cp command to copy a directory along with all subdirectories and files.
What is command?
A command in computing is a request for a computer programme to carry out a particular task. It could be sent using a command-line interface, like a shell, as input to a network service as part of the a network protocol, as an event inside a graphical user interface brought on by the user choosing an item from a menu, or as a command sent to a computer over a network.
The word "command" is specifically used during imperative computer languages. The name was given to these languages because statements in them are frequently written in an imperative mood, which is common in many natural languages. A command is typically compared to a verb in a language where an imperative statement is viewed as being similar to a sentence.
To learn more about command
https://brainly.com/question/25808182
#SPJ4
Most browsers offer this, which ensures that your browsing activity is not recorded on your hard disk.
Answers
The majority of browsers provide a privacy mode that makes sure your browsing history is not stored on your hard drive. People, processes, software, hardware, data, and the Internet make up information systems.
The most widely used encryption protocol on the Internet today is TLS/SSL. TLS/SSL, or Transport Layer Security/Secure Sockets Layer, is an encryption protocol that guarantees the confidentiality of communications between a client and a server. Your browsing history is hidden from other users of the device while you browse privately. Your browsing history and form data are not saved by . When you quit Incognito mode, cookies and site data are removed, but they are remembered while you are browsing.
Learn more about protocol here-
https://brainly.com/question/27581708
#SPJ4